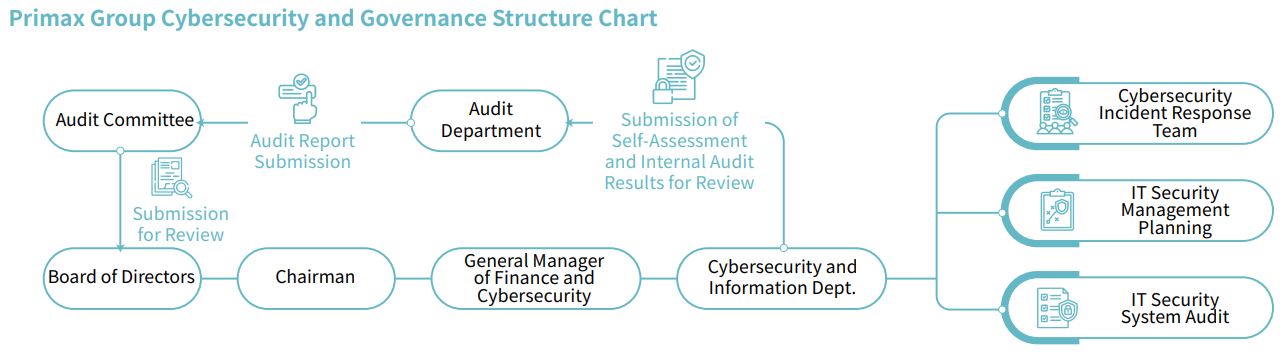
Cybersecurity organizational structure
To improve the security management of the group, a Group Cybersecurity Department has been established, with the Financial and Business Department General Manager as thehighest responsible person. The cybersecurity Department is responsible for driving information security policies and resource allocation. It is staffed with dedicated cybersecurity professionals to ensure that all information security management standards and control measures are effectively and continuously implemented. The organizational structure of the Group's Cybersecurity Department is shown in the figure below:
The organizational structure of the Group's The organizational structure of the Group's Cybersecurity Department
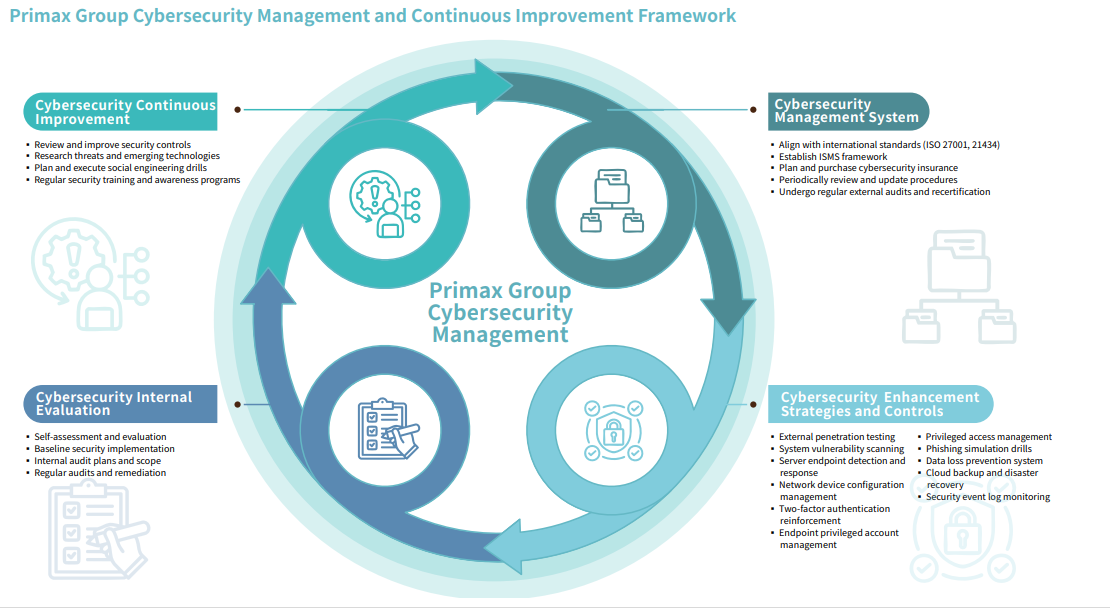
PMX Group's Cybersecurity Management and Continuous Improvement Framework
Cybersecurity management mechanism
All of customer privacy and confidential information is disclosed on a need-to-know basis, and the Group has implemented three different types of control:People, Process and Technology to ensure the security of customer privacy and confidential information. Below is a summary of the three controls:

Cybersecurity management actions
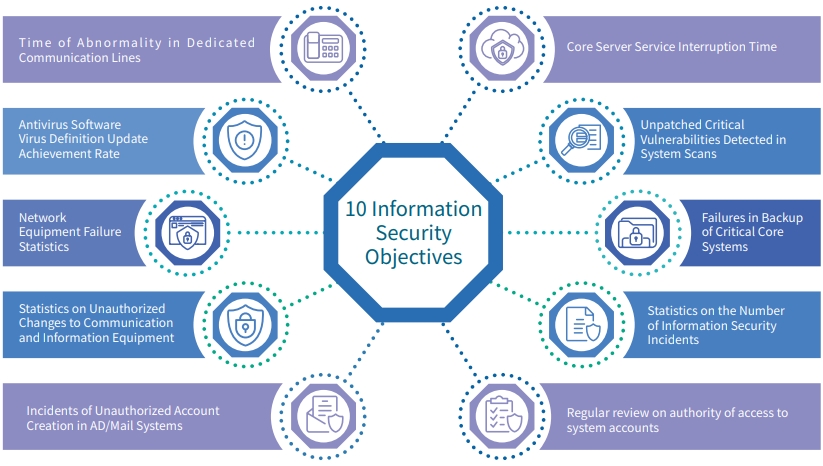
- To meet the requirements of internal information security regulations and external regulatory authorities, the Group has established an Information Security Management System and information security management procedures. Ten information security objectives have been formulated, and the results of their achievement are recorded on a monthly basis.
- To reinforce the information security protection capabilities, we request vendors to perform hacker penetration testing every year to analyze the potential vulnerabilities and scenarios of hacking through various hacking methods, to keep improving the quality of cybersecurity protection.
- In order to enhance the application system security and mitigate risks, we perform system and equipment vulnerability scanning and penetration testing regularly and fix mid-risk and high-risk vulnerabilities each year. Meanwhile, we have also added privileged account access management, IP-guard system, EDR and network equipment configuration management to protect and reduce external intrusion risks and internal sensitive data loss risks, and continue to monitor logs through the information security incident management system to achieve real-time monitoring of abnormality and strengthen the cybersecurity management mechanism.
- For critical systems related to company operations, regular data backups and on-site redundancy mechanisms are implemented to strengthen the enterprise's resilience against cybersecurity risks.
- We organize the information security awareness training for twice per year and 6 social engineering exercises each year, during which it uses a combination of e-mail,instant messaging, and digital TV to communicate with employees on cybersecurity protection and current affairs, which in turn promotes the cybersecurity awareness of the Group's employees. Meanwhile, we have purchased the "CorporateInformation Security Risk Management Insurance/Fraud Risk Protection Insurance"to reduce or shift the losses of cybersecurity, hoping to become an enterprise outperforming in the maturity of information security governance.
-
The Group and its subsidiary, Tymphany Acoustic Technology Limited, obtained new ISO 27001:2022 certificates in December 2024 and September 2024, respectively. The certificates are valid from December 22, 2024 to November 16, 2026, and from September 6, 2024 to September 5, 2027. According to the Group's future information security roadmap, certification scope will be expanded to cover key operational processes in engineering and manufacturing, with annual recertification audits performed by an independent verification body.
Cybersecurity risk assessment
Primax Group takes an inventory of the information assets and update the list of property regularly. Every year, the risks related to the information assets are appraised, and the high risk items are controlled, to lower the chance of risks and their impacts, for the purpose of ensuring the long-term cybersecurity.
Primax has established comprehensive network and computer cybersecurity protection measures; however, malicious hackers can also try to spread computer viruses, destructive software, or ransomware across the Company's network system to interfere with our operations, to extort money, gain control over our computer systems, or spy on confidential information.Such attacks may result in losses due to delay or disruption of orders, or a great cost of remedial and improvement measures adopted to strengthen the Company's cybersecurity systems.
To prevent and reduce the damage caused by such attacks,we continue to update and implement relevant improvement measures, such as strengthening network firewalls and network control; establishing endpoint antivirus measures depending on computer types; adopting new technologies to strengthen data protection and backup; enhancing the detection of phishing emails; and regularly performing social engineering email testing and offering employee IT security awareness training.
Internal audit of cybersecurity
The information audit taskforce of the Cybersecurity Department establishes the assessment indicators based on the risks. The self-assessment and inspection of cybersecurity were completed on March 29 , 2023 . The outcome of assessment and supporting documents were also sent to the Audit Department for verification. The Audit Department implements the PDCA cycle for once per six months. Cybersecurity is one of the required items for audit. All the outcomes of audit are submitted to the Audit Committee and Board of Directors regularly, at least for once per year.
Product R&D and Manufacturing Safety
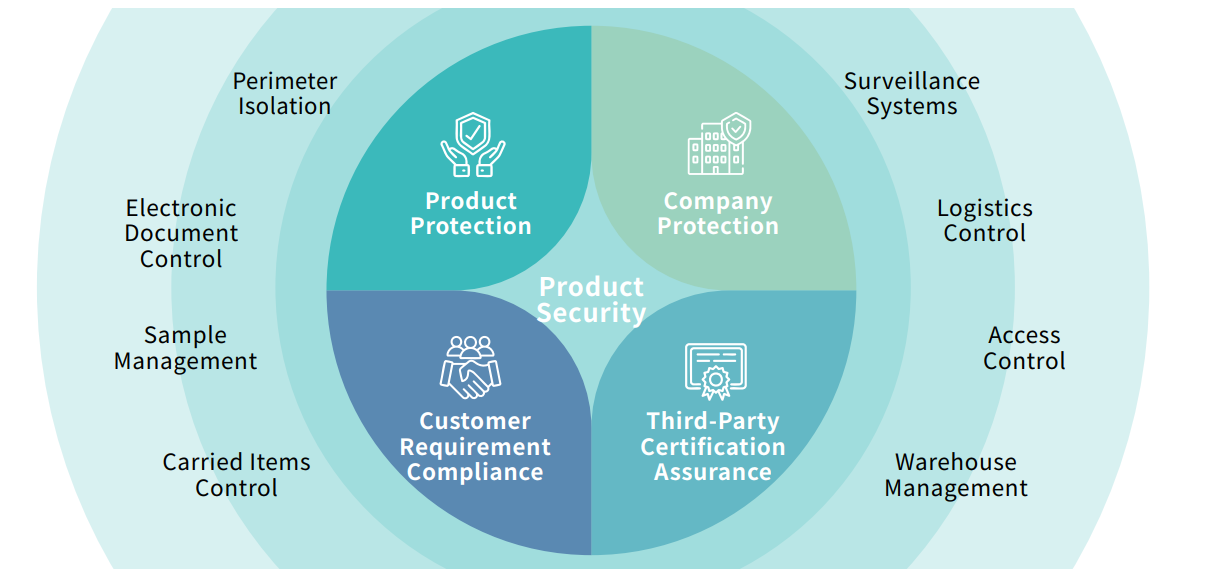
The research and manufacturing units of the company have consistently conducted research and manufacturing operations in accordance with the Group's information security policy and customer requirements and expectations. Through various physical and electronic control processes, the protection of product confidential information and process technology is ensured, while also maintaining compliance with customer requirements and relevant third-party certifications.
Primax Group's products include both computer peripheral products and non-computer peripheral products. If products are classified according to their information security risk characteristics, such as electroacoustic products, OEM brand products, and wireless connector products, we will arrange control measures,such as code review or source code scanning, per customer's request before software/firmware updates go live to reduce the information security risks.
At the stages from R&D to shipment of finished products, we always follow the customer's security principles. Any security-related concerns are immediately corrected. Without affecting the production process and subsequent operating procedures, we ensure the product information security without worry. Moreover,we also place significant emphasis on post-shipment product information security. Depending on the product's characteristics and customer requirements, preventive measures such as software testing or physical circuit isolation are implemented to strictly prevent potential cybersecurity risks during product use (e.g., malicious program implantation) and avoid the risk of user information leakage.
Customer Privacy and Personal Data Protection
Primax Group complies with applicable domestic and international personal data protection laws and regulations and has established a Privacy Policy. The Cybersecurity and Information Department serves as the dedicated unit responsible for personal data protection management. Both Primax and Tymphany each have one designated staff member responsible for establishing relevant regulations, handling complaints, and managing operational processes related to personal data protection.
At the same time, Primax Group is committed to safeguarding customer information security to protect customer interests. Policies and procedures have been established for managing customer privacy and confidential information, based on the principle of "least privilege." Access to sensitive information relevant to customer projects is granted only to individuals who obtain internal authorization. The Cybersecurity and Information Department periodically reviews information security procedures to ensure they are updated in a timely manner and that security measures remain aligned with customer requirements and expectations.
Primax respects the rights of data subjects to exercise their legal entitlements concerning personal data. A dedicated contact email is provided on the Company website. If complaints are received or any personal data breaches are identified, the matter will be handled in accordance with the applicable policies, including the Personal Data Protection Policy, Supplier Code of Conduct, or Customer Data Confidentiality Agreement, and any necessary corrective or disciplinary actions will be taken. In 2024, zero incidents of personal data violations or customer privacy breaches were recorded, including complaints.

